
Google has given webmasters their final warning to convert their sites to HTTPS or be branded as “Not Secure” with a prominent message in the browser bar of all Chrome and all Chrome-based browsers after October of this year.
Why is Google doing this?
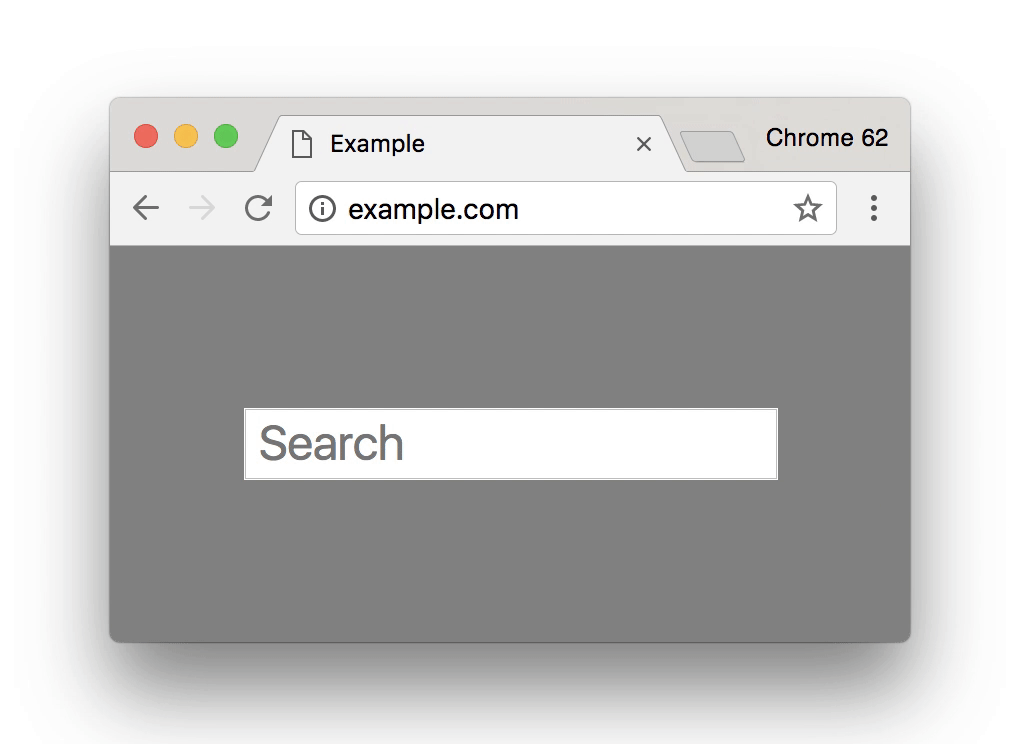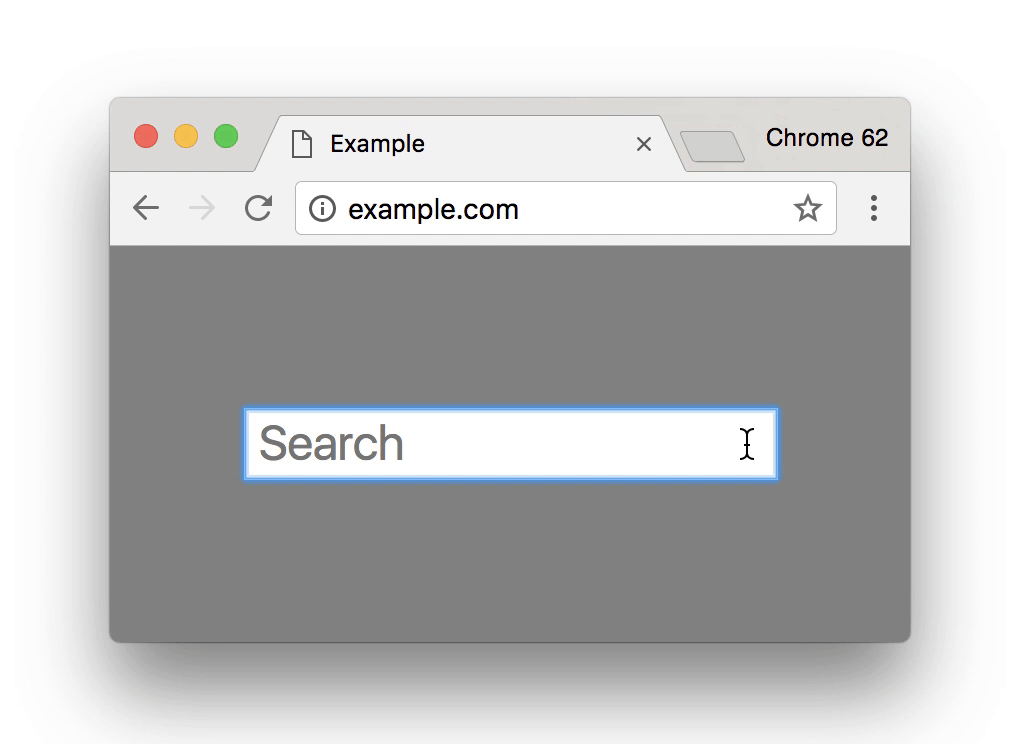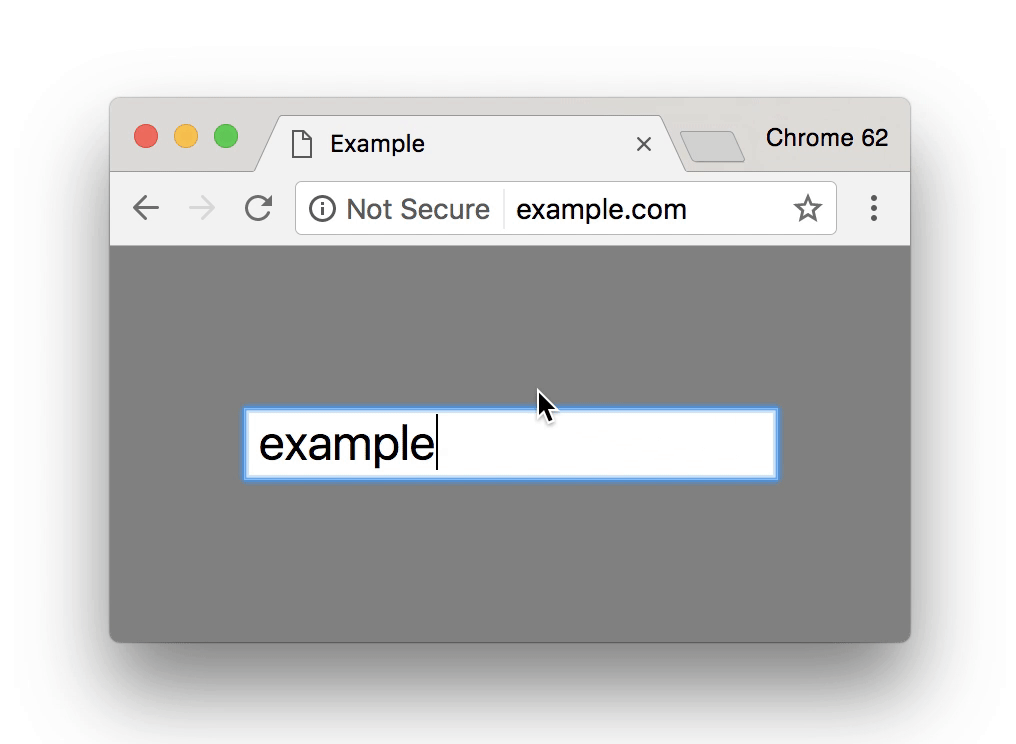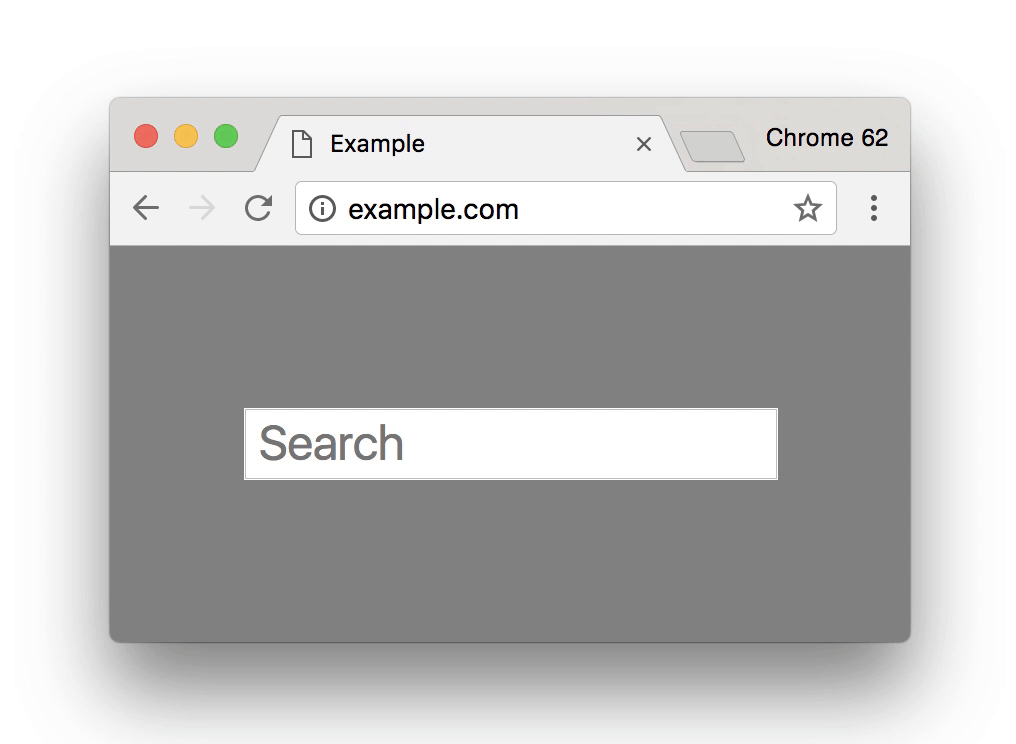
Google has been urging webmasters to switch their sites to the more secure HTTPS security protocol for years, using increasingly drastic measures. Currently, Google is denoting sites that are secure using a green icon in the browser bar. Since so many sites have now adopted the protocol, Google is taking this a step further with a prominent red warning for sites that are not secure.
What does this mean for you?
Internet users don’t give up their information easily. They have to trust that you won’t let their data be breached or misuse their information. If they see that your site is specifically “Not Secure”, they simply aren’t going to trust you with anything.
That could mean increasing bounce-rates for your website, fewer e-commerce sales, fewer newsletter sign-ups, or fewer internet-driven leads for your business.
Two-Stage Roll Out
Rather than “switching on” the security warnings all at once, Google will be rolling out the change in two steps.
First, Chrome will remove the green icon signifying safe websites from browser bars. In its place, they will temporarily leave the small lock icon in its place.
Then, beginning in October, Google will introduce the official red icon identifying sites that are “Not Secure.”
This latest warning from Google gives webmasters plenty of time to make the switch, but I advise taking action sooner rather than later. You can get started right now with Google’s HTTPS set-up guides here.





 A few weeks ago, Google
A few weeks ago, Google 


