Google announced recently that it is requiring advertisers to provide documentation of their identity and geographic location to be eligible to run ads on the platform.
The new policy is an expansion of similar restrictions put in place in 2018 requiring the advertisers behind political ads to provide identification verification.
How Advertisers Verify Their Identity
Google is rolling out the new policy in phases and will be selecting certain advertisers to verify themselves first. Specifically, Google says it will prioritize those who do the following across its Ad Network:
- Promotion of products, goods, and services.
- Examples: Retail, media and entertainment, travel, B2B, technology, etc.
- Promotion of informational, advisory, or educational content.
- Examples: Content promoting educational resources, research and statistics, free health or financial advice, charitable or social causes, etc.
- Promotion of content related to regulated industries.
- Examples: Gambling and games, financial products or services, healthcare products or services etc.
If selected, an advertiser will be required to provide documentation to verify their identity within 30 days. Accepted documentation will include:
- Personal identification methods
- Business incorporation documents
- Possibly other items to verify who they are
- Operating geography
If documentation is not provided within the 30 day limit, all ads will be stopped until the issue is resolved.
Google also says it will begin the program in the United States before rolling out globally. The new requirements will apply to every aspect of Google’s multi-faceted advertising platform, including Search, Display, and YouTube ads.
Currently, the company expects that it will take a few years to fully implement the program.
Notably, the information currently available suggests that Google is specifically focusing on the individuals or companies running the ads, not necessarily the individual managing the ads. This means your ad agency will likely be asked to verify your identity on your behalf.
New Disclosures For Ads
Part of the reason Google is requiring this information, is that it is beginning to add new disclosures about the identity of advertisers when displaying paid ads.
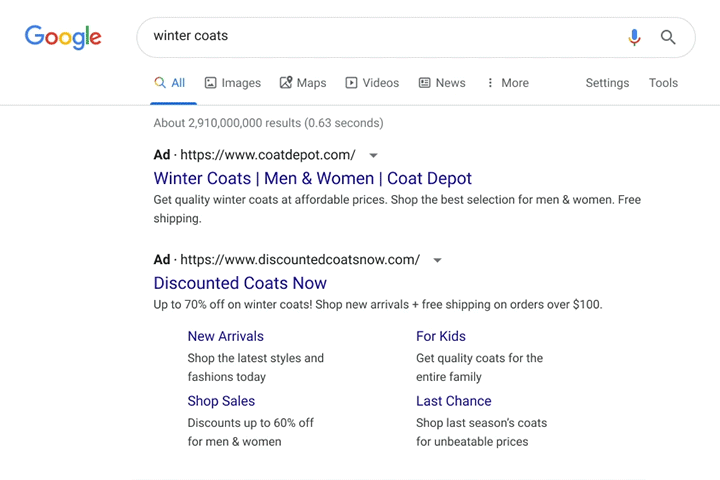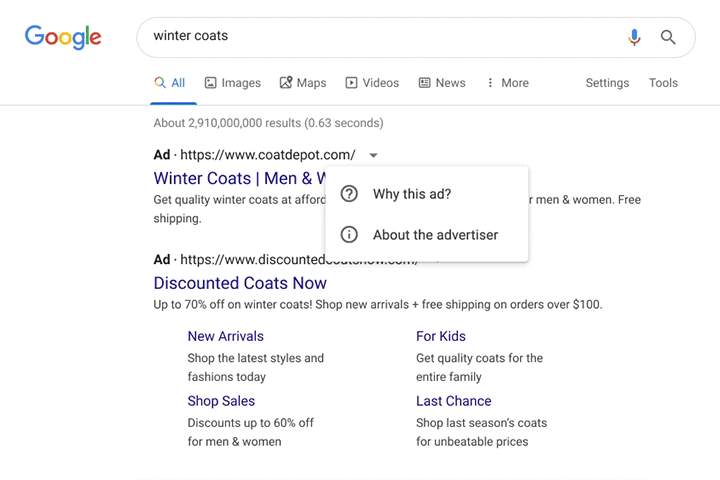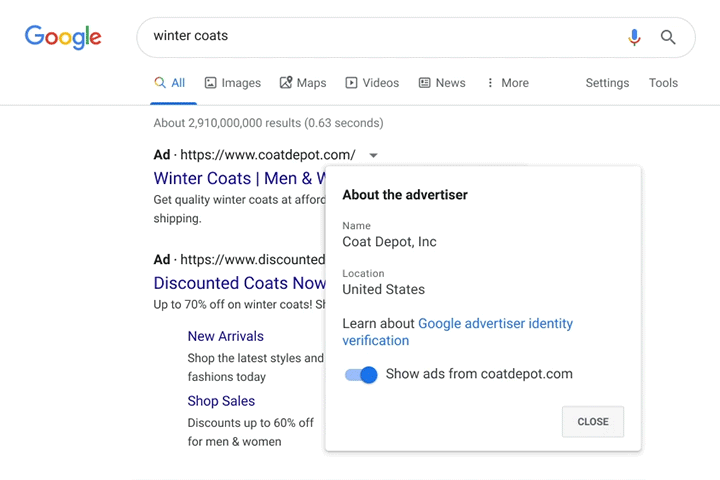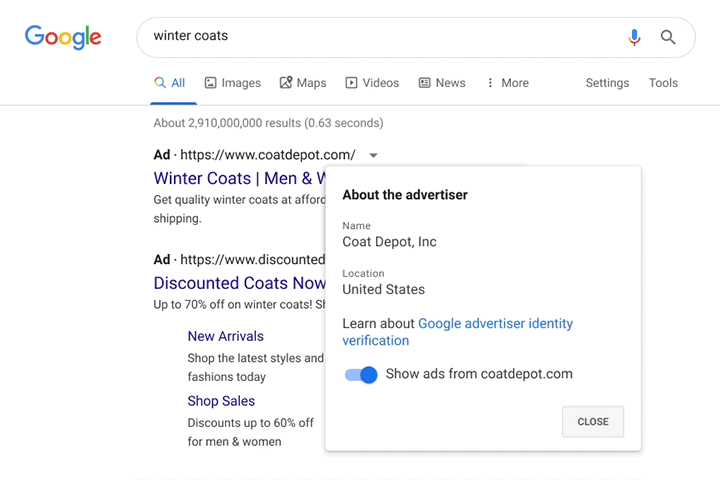
Image Source: Susan Wenograd/Search Engine Journal
The disclosures are available below the “Why this ad?” option when clicking for more details.
The disclosure will include information about the advertisers’ name, country location, and will provide an option to stop showing ads from that advertiser.
Why Is Google Doing This?
As the company explained in its announcement, the new program is part of a larger effort to “provide greater transparency and equip users with more information about who is advertising to them.”
Director of Product Management for Ads Integrity, Jack Canfield, elaborated by saying:
“This change will make it easier for people to understand who the advertiser is behind the ads they see from Google and help them make more informed decisions when using our advertising controls. It will also help support the health of the digital advertising ecosystem by detecting bad actors and limiting their attempts to misrepresent themselves.”
For more information, read Google’s announcement here or explore their additional guidance on the program here.